You've probably experienced 3DS without knowing it. It’s that extra verification step during online checkout: you’re redirected to enter a code sent to your phone or a popup asks you to confirm your purchase through your bank’s app. For many consumers, it’s a minor inconvenience. For card issuers, it presents a critical risk management challenge.
3DS (3-Domain Secure) gets its name from the three domains that coordinate to verify a cardholder’s identity: the issuer domain (the card program), the acquirer domain (the merchant), and the interoperability domain (the card network infrastructure). When these three domains work together, they create a framework designed to prevent fraud. The reality, however, is more complex.
Based on a study by Datos Insights, merchants strategically trigger 3DS for their highest-risk transactions—those they already suspect may be fraudulent. When authentication succeeds, fraud liability automatically transfers to the issuing card program. Card programs cannot opt out of this process. When issuers lack active 3DS management systems, the card networks make authentication decisions on their behalf, approving nearly every request and transferring the associated high-risk liability.
The consequences of liability-shifted transactions are serious, but they don’t have to be inevitable. Taking control of the 3DS authentication process presents a massive opportunity for card programs. Each 3DS authentication request includes extensive intelligence data: over 150 possible data points about the cardholder’s device, location, behavior, and transaction patterns. The same protocol that creates liability exposure also delivers sophisticated fraud signals unavailable in standard authorization flows.
At Lithic, we’re on track to process more than 5 million 3DS authentications this year across our client base. This scale has reinforced a critical insight: programs that accept network defaults forfeit both control and opportunity, while those with active involvement transform mandatory participation into competitive advantage. For card programs, understanding 3DS and implementing the right solution makes the difference between a liability nightmare or a transaction data goldmine.
The 3DS Framework: Risk and Opportunity
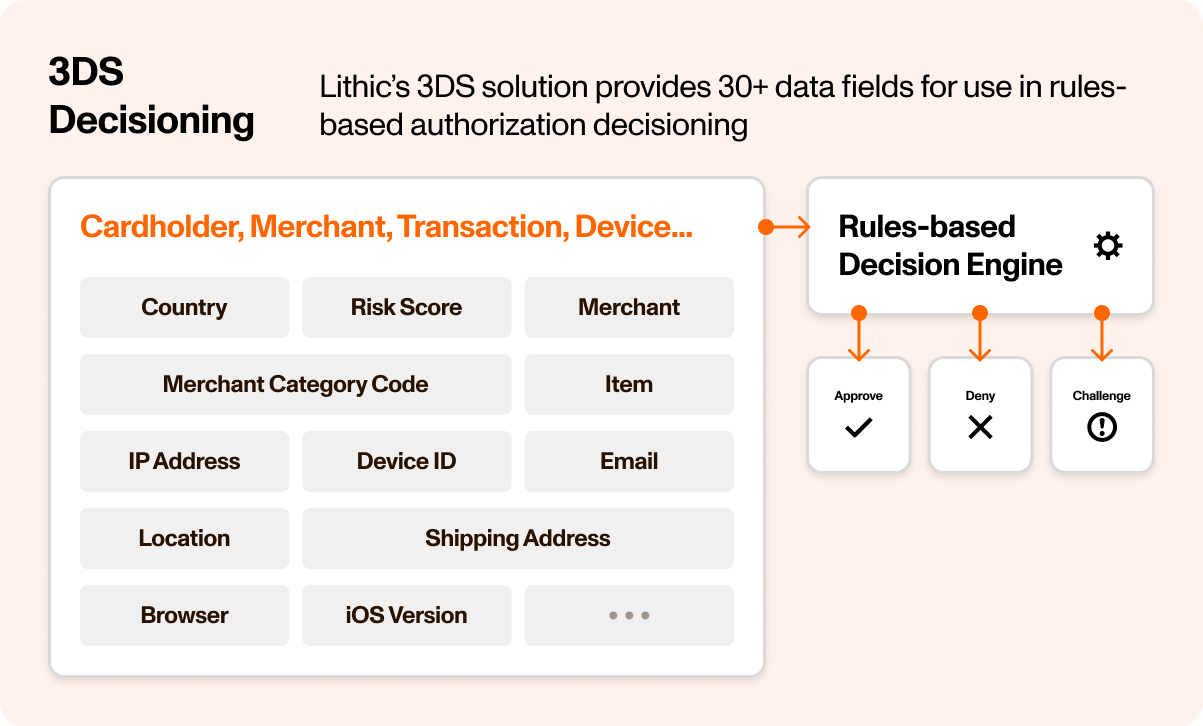
The intelligence opportunity in 3DS lies in the sheer volume and quality of data transmitted with each authentication request. While standard authorization messages contain basic transaction details, 3DS delivers forensic-level intelligence through the Enhanced Message Extension (EMV 3DS 2.0). This protocol requires a minimum of 20 data points and supports over 150 data elements that paint a comprehensive picture of the transaction environment.
This data richness creates compelling fraud detection opportunities for prepared card programs. Consider what arrives with each authentication request through Lithic’s API:
- Device intelligence: Browser fingerprints including IP addresses, user agents, JavaScript capabilities, and time zones that reveal automated attacks. For mobile apps, detailed device data including platform, OS version, screen resolution, and geolocation coordinates
- Cardholder verification: Email addresses, phone numbers (home, mobile, and work), and both billing and shipping addresses that enable real-time identity validation against your KYC records
- Merchant risk signals: Merchant category codes, risk indicators including delivery timeframes, shipping methods, and whether items are being reordered. Special flags for gift card purchases and pre-orders that often signal fraud
This data richness creates compelling fraud detection capabilities. According to data from Datos Insights, fraud rates are three to six times lower in regulated markets where up to 50% of CNP transactions are protected by 3DS. But the benefits extend beyond individual transaction decisions.

Each authentication builds a comprehensive risk profile that improves subsequent authorization accuracy. When the same transaction arrives for authorization moments later, issuers already possess deep context about device authenticity, behavioral patterns, and risk signals. This pre-authorization intelligence enables precise decisioning that reduces both fraud losses and false declines. The same Datos Insights research shows that in the UK, card authorization approval rates rise to 90-96% when 3DS protects CNP transactions, versus just 70-75% without 3DS.
The fundamental challenge remains unchanged though: 3DS operates as an opt-in for merchants but mandatory for issuers. Merchants choose when to invoke 3DS, typically for transactions they deem risky or for regulatory compliance. Issuers cannot refuse when selected. Without an active 3DS solution, networks automatically evaluate these authentications, shifting liability by default without sharing this rich device and behavioral data. But with proper implementation, this mandatory participation becomes an intelligence advantage rather than a liability burden.
Lithic's Multi-Layer Defense Strategy
Most card programs discover 3DS problems the hard way. Rising chargeback rates reveal that merchants have been routing high-risk transactions through 3DS, successfully shifting liability. Fraud teams must then identify which authentication patterns drive losses while simultaneously managing false decline rates that impact cardholder satisfaction and revenue.
The fundamental challenge is that issuers require control at multiple decision points. They need real-time authentication evaluation capabilities, configurable rules for identified fraud patterns, and selective challenge mechanisms that verify suspicious transactions without degrading the customer experience. Without these capabilities, programs face an unacceptable trade-off between fraud exposure and transaction approval rates.
At Lithic, we designed our 3DS solution around three critical control points that address these operational requirements. Regardless of the implementation model selected, Lithic provides comprehensive personal, device, and behavioral data from the 3DS process for every authentication, ensuring programs have the intelligence necessary for informed decisioning.
Taking Control of Authentication Decisions
Every issuing program must determine whether to build authentication decisioning capabilities internally or leverage a managed solution. This decision depends on existing fraud infrastructure and technical resources.
Lithic Decisioning serves programs that require sophisticated fraud detection without the operational complexity of building proprietary systems. When authentication requests arrive, our fraud engine performs real-time enrichment by matching account holder KYC attributes against cardholder details such as name and email. The system analyzes IP metadata to identify VPN usage and geographic inconsistencies. For mobile transactions, device information including locale, time zone, and geolocation is parsed and evaluated. These signals inform models trained on network-wide fraud patterns while maintaining issuer-specific optimization parameters. Programs receive detailed authentication data via webhooks for monitoring and analysis, gaining actionable risk intelligence without the overhead of operating real-time decisioning infrastructure.
Customer Decisioning provides established programs with complete control by routing authentication requests directly to their external endpoints. Issuer systems simply must respond with an approve, decline, or challenge decision. This structure provides complete control for programs with advanced risk infrastructure, enabling card programs to evaluate transactions according to their risk tolerance and business rules while retaining full authority over liability.
Targeting Specific Fraud Patterns
Even sophisticated decisioning models benefit from rule-based interventions for identified fraud patterns. For example, programs may determine that gaming merchant transactions from specific countries generate disproportionate fraud, or that cryptocurrency purchases above certain thresholds consistently result in losses.
Lithic’s 3DS Authentication Rules enable programs to codify these patterns into automated responses. Authentication Rules evaluate merchant category codes, countries, currencies, transaction amounts, risk scores, merchant descriptors, and more. Combining multiple attributes allows precise targeting of fraud patterns while preserving legitimate transaction approval rates. For example, rules blocking authentications on high-value foreign-currency purchases from high-risk countries won’t affect established cardholders making routine online purchases.
The Lithic Authentication Rules framework also provides data-driven validation before production deployment. Programs can operate rules in shadow mode to evaluate performance against live authentications without affecting transaction outcomes. Backtesting capabilities demonstrate how rules would have performed against historical transaction patterns. This methodology enables rule refinement based on actual performance data rather than theoretical assumptions.
Challenge Orchestration
While the rich authentication data provided by merchants can often support reliable identity decisions, legitimate cardholders routinely place transactions that look suspicious on paper. Consider a cardholder that has traveled home for the holidays, ordering some last-minute decorations with rush shipping. This legitimate cardholder has placed a high-value order from a new device, the IP geolocation does not match recent history, and the shipping address has never been used before. The merchant invokes 3DS, and passive risk signals are not sufficient to clear the transaction. The issuer now needs a controlled way to verify the cardholder without defaulting into either a false decline or merchant-selected liability. That control point is the 3DS challenge.
If device and behavioral data alone is not enough to verify cardholder identity, issuers can step up to a 2FA flow. Lithic offers two orchestration models to match different operational capabilities and customer experience priorities.
Lithic Orchestration provides a turnkey solution for programs that want challenge capabilities without building authentication infrastructure. When your decisioning logic determines a transaction requires step-up verification, Lithic handles the complete flow via SMS one-time passcodes. Passcode generation, delivery, cardholder verification, and response processing all happen automatically within network-mandated timeframes. Programs can customize SMS templates and UI styling to maintain brand consistency while Lithic manages the technical execution. The only requirement is maintaining current cardholder phone numbers in the Lithic system.
Customer Orchestration provides complete control over challenge delivery for programs that want to manage the authentication experience directly. Issuer systems receive challenge requests from Lithic and deliver verification through whatever channels fit their strategy—SMS, email, push notifications, in-app biometric verification, or proprietary methods. Programs collect cardholder responses, communicate results back to Lithic within the challenge window, and maintain full authority over the customer experience. Lithic manages network communication and protocol compliance while programs control how cardholders interact with authentication. This model suits programs with established cardholder communication infrastructure or specific authentication requirements that want complete control.
Integration with Authorization
Authentication and authorization are separate decision points, but they shouldn't operate in isolation. The intelligence gathered during 3DS authentication becomes most valuable when it also informs the final authorization decision. Without this connection, programs miss critical fraud signals that could prevent losses before they materialize.
Consider a fraudster who attempts to complete a stolen card transaction and fails 3DS challenge authentication. They can’t provide the correct one-time passcode because they don't have access to the legitimate cardholder’s phone. The merchant, unwilling to lose the sale, proceeds to submit the transaction for authorization anyway, hoping the issuer will approve it despite the failed authentication. Without visibility into the authentication outcome, issuer authorization logic treats this the same as any other transaction. The fraudulent purchase goes through.
Technically, the issuer retains chargeback rights when authentication fails. The liability didn’t shift. But chargebacks take time and operational resources to pursue, and the real opportunity is stopping the fraud at authorization time before it becomes a dispute.
To close this gap, programs need authentication context available when making authorization decisions. Lithic makes this data accessible in both our authorization decisioning products, Authorization Rules and ASA (Authorization Stream Access). In Auth Rules, programs can apply additional scrutiny to transactions where liability has shifted from 3DS authentications. In ASA, the cardholder_authentication object includes critical fields to power decisioning logic: a liability_shift indicator, authentication_result, and three_ds_authentication_token linking the full authentication data to the authorization. These fields enable issuer authorization logic to consider authentication context when making final transaction decisions.
Failed authentications followed by authorization attempts are exactly the types of transactions that warrant heightened scrutiny. By integrating authentication results into authorization logic, programs transform authentication failures into actionable decline signals, stopping fraud at the point of decision rather than managing it through disputes afterward.
Shifting 3DS from Liability Burden to Intelligence Asset
3DS adoption continues expanding worldwide. European PSD2 requirements drove near-universal adoption for online transactions as mandates rolled out 2019-2021. Japan implemented universal 3DS 2.0 requirements earlier this year and similar mandates are emerging across other Asia-Pacific markets. Even in the U.S., where 3DS remains optional, adoption is growing rapidly. Despite only 3% of card-not-present transactions currently using 3DS in North America, that rate is climbing with year-over-year growth exceeding 30% as CNP fraud drives merchant adoption.
The fundamental tension between merchants and issuers around liability will persist as adoption scales. Merchants route their riskiest transactions through 3DS to shift exposure and issuers absorb that transferred liability. This adversarial dynamic isn't going away. What changes is how prepared programs are to handle it.
Programs that treat 3DS as pure compliance overhead will continue seeing it as a liability trap. Those that recognize the intelligence opportunity and implement sophisticated decisioning can turn mandatory participation into competitive advantage. The difference comes down to having the right infrastructure in place: real-time visibility into authentication requests, configurable rules for identified fraud patterns, device fingerprinting and IP intelligence that goes beyond basic network scores, and access to authentication context during authorization decisions.
For ambitious teams evaluating issuer processing providers, these capabilities separate solutions built for scale from those checking a compliance box. The authentication data flowing through 3DS represents one of the richest fraud intelligence streams available to issuers, and programs that capture and act on it systematically will outperform those that don’t. In a landscape where every basis point of fraud matters, that choice defines program success.
Ready to explore how 3DS can transform your card program? Get in touch with our team to learn more about implementing 3DS and intelligent data authentication for your program.

